Introduction
Whenever you prepare a vSphere cluster in NSX, the distributed firewall is enabled automatically on all ESXi hosts in that cluster. One of these clusters can be your management cluster where several management VMs are running including the vCenter server which provides the GUI interface for managing your NSX solution.
As you always aim to have a zero trust model while opening only specific needed traffic ports for applications and VMs and blocking all other traffic, you can end up with a situation where you block yourself from the DFW management interface if you mess up with the rules. In this case you will block access to the vCenter and you will loose the capability to fix the DFW rules.
Offcourse this situation can be sorted out but through calling a REST API in this case. You can have a look at the below VMware KB article to see how you can do so:
https://kb.vmware.com/s/article/2079620
NSX components are implicitly included in the DFW exclusion list which will exclude these VMs from any enforced firewall rules. However, to protect yourself, VMware recommends that you explicitly add management VMs like vCenter to the DFW exclusion list to avoid situations where you may block yourself.
The main purpose of this blog is to show you how we can validate that the vCenter VM is effectively added to the DFW exclusion list via central CLI. However I will start first by showing you how we can add vCenter to the exclusion list then we will go directly to our main topic.
Add vCenter to DFW exclusion list
To add the vCenter virtual appliance to the DFW exclusion list with NSX 6.4.1:
Navigate to Menu > Network and Security tab.
Click on Firewall settings and navigate to Exclusion list tab.
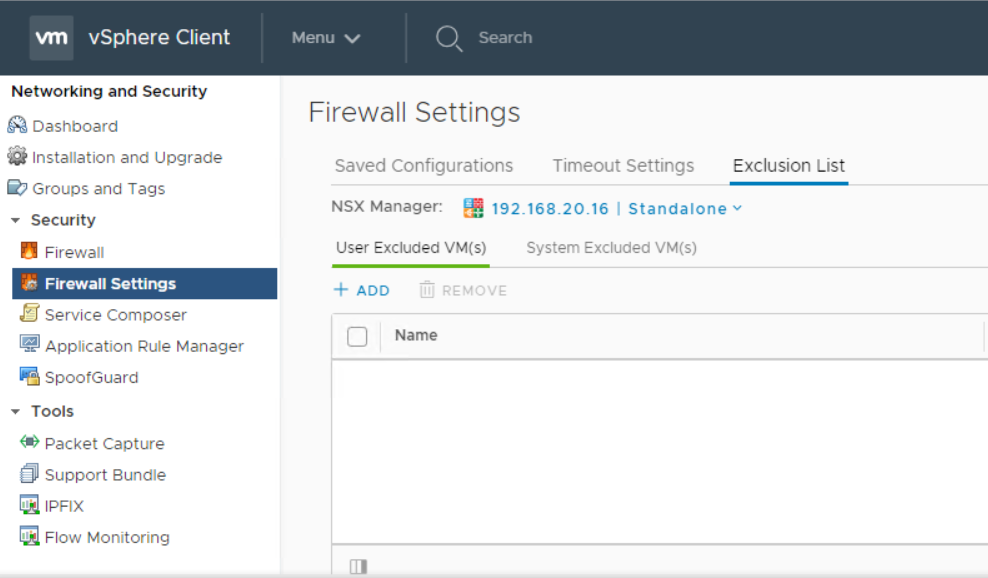
You can notice a nice new enhancement in NSX 6.4.1 is the differentiation between system excluded VMs (NSX components) and user excluded VMs (like vCenter). Click on + ADD button.
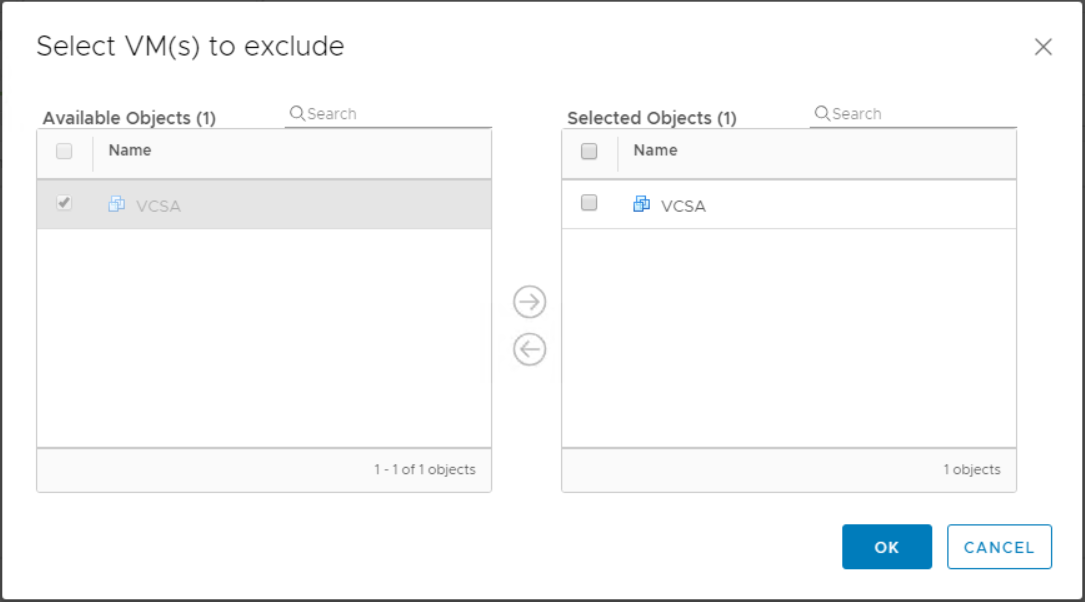
Add the vCenter Server virtual machine and click OK.
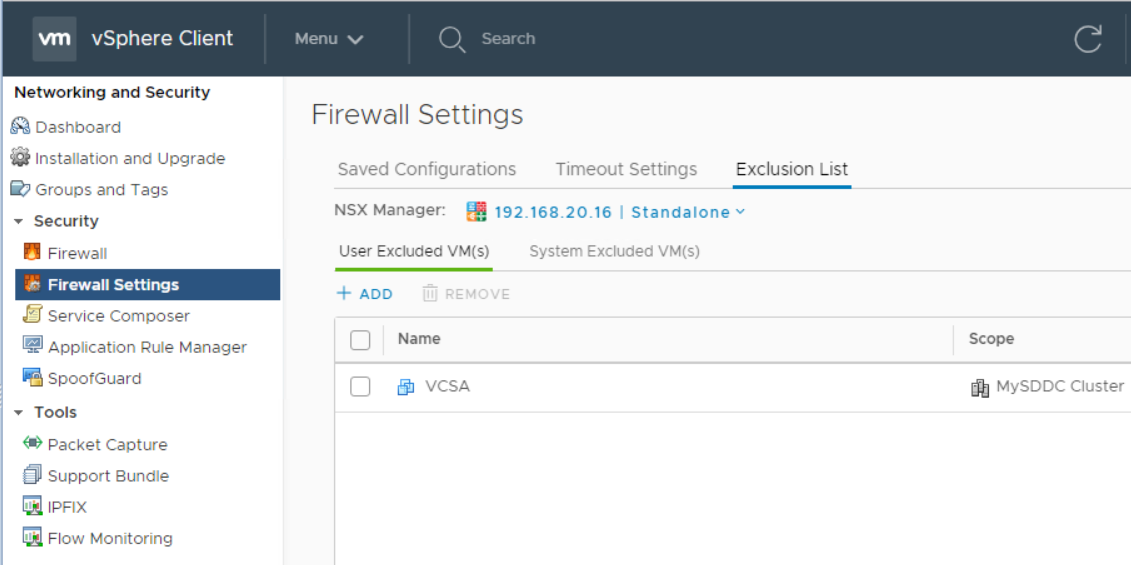
Now your vCenter VM is excluded from all enforced firewall rules. This will be applied to all vNICs of the added VM (in case it is multi-homed).
How can we validate via Central CLI ?
SSH to your NSX Manager using your favorite SSH client (ex: Putty).
Get the Cluster IDs:
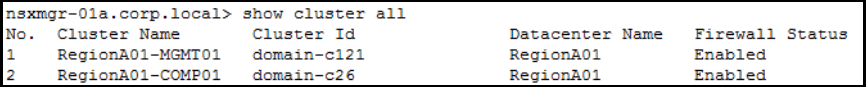
Get the Host IDs:
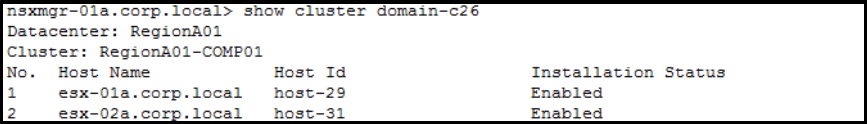
Get the VM IDs:
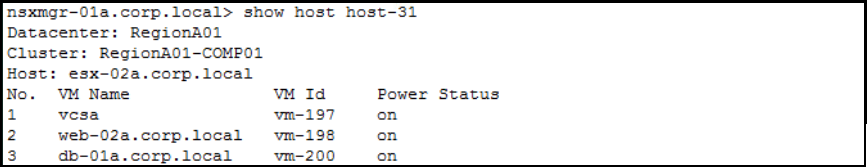
Get the dvfilters applied to vCenter VM (before adding vCenter to DFW exclusion list):
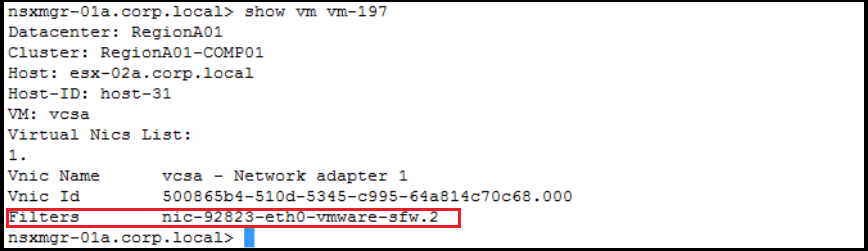
Get the dvfilters applied to vCenter VM (after adding vCenter to DFW exclusion list):
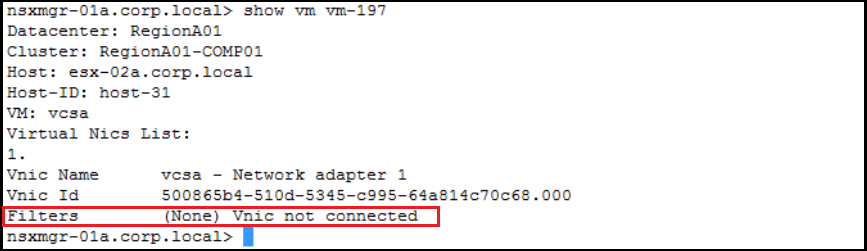
You can notice that no dvfilters at all are applied to the VNIC of the vCenter after adding it to the DFW exclusion list thus no firewall rules will be enforced.
Thanks for reading,
Hope this post is informative,
Mohamad Alhussein

